For some time I see all kinds of options to use Azure files, have some great ideas and thoughts. Connecting this over the vpn of use the azure files with a dfs. Useful maybe ? fun absolutely building things just a way that is maybe a bit different is fun and you may see other opportunities on how to use the resources.
Using Azure Files is not new, But using Azure files with Active directory Authentication is a long waited feature and now that it is GA we can use this.
Azure Files is a shared storage service that lets you access files via the Server Message Block (SMB) protocol, and mount file shares on Windows, Linux or Mac machines in the Azure cloud.
Azure Files supports identity-based authentication over Server Message Block (SMB) through two types of Domain Services: Azure Active Directory Domain Services (Azure AD DS) (GA) and Active Directory (AD).
Azure file shares only support authentication against one domain service, either Azure Active Directory Domain Service (Azure AD DS) or Active Directory (AD).
AD identities used for Azure file share authentication must be synced to Azure AD. Password hash synchronization is optional.
AD authentication does not support authentication against Computer accounts created in AD.
So what would be the option to use this, As a Cloud file share, in WVD or RDS, you can connect this directly to your clients if needed.
AD authentication can only be supported against one AD forest where the storage account is registered to. You can only access Azure file shares with the AD credentials from a single AD forest by default. If you need to access your Azure file share from a different forest
Azure Files supports Kerberos authentication with AD with RC4-HMAC encryption. AES Kerberos encryption is not yet supported.
So how to start with Azure Files. In this blog post I created a Powershell script that does the most of the Config to get you started with Azure Files.
First we need to address some parameters
#ResourceGroup name and location
$RG="rsg-blog-fileshare20"
$Location="eastus2"
$storageaccount="storfileserver20"
$shareName = "blogshare01"
These basis are needed to create the Azure resources but there is also a Special PowerShell module needed AzFilesHybrid Download and unzip the AzFilesHybrid PowerShell module
This module can be download from github and extracted on your machine
You may need to set the executionPolicy
#Azure file modules
#Set-ExecutionPolicy -ExecutionPolicy Unrestricted -Scope Currentuser
cd c:\AzFilesHybrid
Unblock-File .\CopyToPSPath.ps1
.\CopyToPSPath.ps1
The CopyToPSPath.ps1 will load the modules that are needed for this.
Our next step is importing the module AzFilesHybrid
Import-Module -name AzFilesHybrid -Force
Our next step is connect to our Azure subscription
#Connect to Azure
Connect-AzAccount
#Select the target subscription for the current session use your subscription ID
Get-AzSubscription
Select-AzSubscription –SubscriptionId 11111111-1111111111-111111111-11111-1
Now that the Azure subscription is connected we make a resource group and the storage account with the share.
#create Rsource group
New-AzResourceGroup -Name $RG -Location $Location
#create storage account
New-AzStorageAccount -ResourceGroupName $RG -Location $Location -Name $storageaccount -SkuName Standard_LRS -AccessTier Hot
#create storage Fileshare
New-AzRmStorageShare -ResourceGroupName $RG -StorageAccountName $storageaccount -Name $shareName -QuotaGiB 1024 #| Out-Null
Now that the storage account is created and the share we make a computer account for the AD rights, optional is the OU location where the computer account is stored.
Important action het is that this should run on a domain joined computer, as it needs to have access to the domain to create the computer account. Needless to say but you need a proper AD account to create the Computer account.
#join azure files to AD
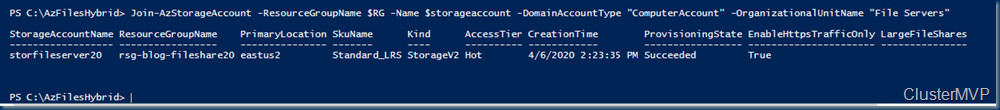
Join-AzStorageAccount -ResourceGroupName $RG -Name $storageaccount -DomainAccountType "ComputerAccount" -OrganizationalUnitName "File Servers"
Now that the computer account is created we can move to the next steps, As I want to add a privatepoint and make sure my local DNS can find the fileshare.
So how does this look like in the Azure portal.
Here is the fileshare and file server with all the configuration options
The share is AD ready. The Option is enabled and ready to use
Now that we have the share in place we can configure the share. First we test the Connection from the Server to the Azure file share.
#test SMB connection
Test-NetConnection -ComputerName storfileserver20.file.core.windows.net -CommonTCPPort SMB
The file share can be used, but wait there is more, it al depends on your configuration. If you use the share only in Azure then DNS forwarders are not need, but just in case.
This works but we will create an endpoint now to make sure the share is not listening to all requests
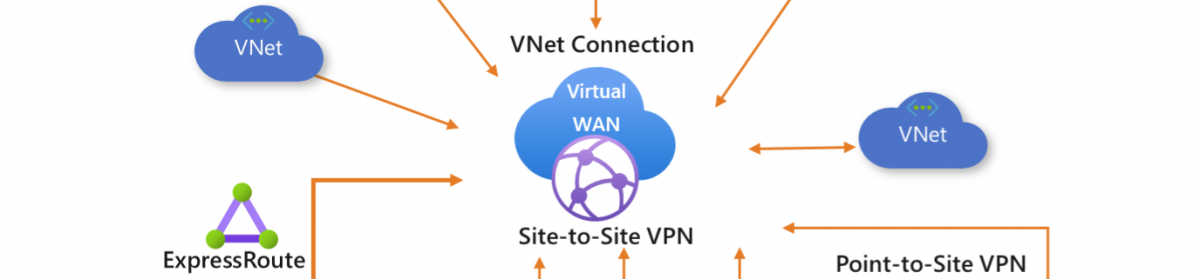
You can use private endpoints for your Azure Storage accounts to allow clients on a virtual network (VNet) to securely access data over a Private Link. The private endpoint uses an IP address from the VNet address space for your storage account service. Network traffic between the clients on the VNet and the storage account traverses over the VNet and a private link on the Microsoft backbone network, eliminating exposure from the public internet.
Using private endpoints for your storage account enables you to:
- Secure your storage account by configuring the storage firewall to block all connections on the public endpoint for the storage service.
- Increase security for the virtual network (VNet), by enabling you to block exfiltration of data from the VNet.
- Securely connect to storage accounts from on-premises networks that connect to the VNet using VPN or ExpressRoutes with private-peering.
Creating the Private endpoint is a bit tricky in PowerShell and quicker in the GUI if you do this in several steps as in the blog post.
So we give the Connection a name and place it in a region
Selecting the Resource that we want to point, in this case it is the Files server and I bind this to the Network
All the steps are completed.
Now that the PrivateLink is created We add the DNS zone if not already done. this is needed when local Clients “on-premises” want to connect to the share
This DNS zone is needed as we want to access from the on-premises Machine to the Azure share. connected over the VPN tunnel. You can also choose to connect over the internet, Or have the option to add the Azure file share to the DFS
First we are making a DNS forwarder rule that is needed for the creating DNS forwarding rule set, which defines which Azure services you want to forward requests.
$ruleset=New-AzDnsForwardingRuleSet -AzureEndpoints StorageAccountEndpoint
$ruleset.DnsForwardingRules
The Core.windows.net forwarder is needed. the IP 168.63.129.16 is the Microsoft DNS
# Deploy and configure DNS forwarders
New-AzDnsForwarder -DnsForwardingRuleSet $ruleSet -VirtualNetworkResourceGroupName "rsg-vnet-sponsor01" -VirtualNetworkName "Azure-vnet-sponsor01" -VirtualNetworkSubnetName "Management"
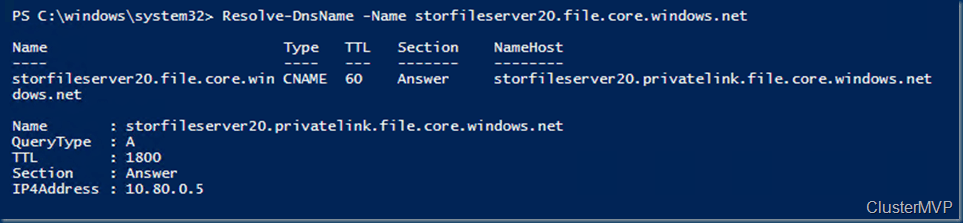
Confirm DNS forwarders:
Resolve-DnsName -Name storfileserver20.file.core.windows.net
Make sure you configure on the on-premises DNS the Forwarder to the Azure DNS, in this case to my Azure AD VM that runs also DNS
Now that the DNS is in place we can connect to the Azure files share in the cloud but also on premises with the connection routed to the VPN tunnel instead of direct to the internet.
Setting Permissions on the Azure Files Shares is not complicated.
With the general availability of AADDS authentication for Azure Files, Microsoft introduced three Azure built-in roles for granting share-level permissions to users:
•Storage File Data SMB Share Reader allows read access in Azure Storage file shares over SMB.
•Storage File Data SMB Share Contributor allows read, write, and delete access in Azure Storage file shares over SMB.
•Storage File Data SMB Share Elevated Contributor allows read, write, delete and modify NTFS permissions in Azure Storage file shares over SMB.
Azure Files supports the full set of NTFS basic and advanced permissions. You can view and configure NTFS permissions on directories and files in an Azure file share by mounting the share and then using Windows File Explorer or running the Windows icacls or Set-ACL command.
To configure NTFS with Admin permissions, you must mount the share by using your storage account key from your domain-joined VM.
The following sets of permissions are supported on the root directory of a file share:
- BUILTIN\Administrators:(OI)(CI)(F)
- NT AUTHORITY\SYSTEM:(OI)(CI)(F)
- BUILTIN\Users:(RX)
- BUILTIN\Users:(OI)(CI)(IO)(GR,GE)
- NT AUTHORITY\Authenticated Users:(OI)(CI)(M)
- NT AUTHORITY\SYSTEM:(F)
- CREATOR OWNER:(OI)(CI)(IO)(F)
Mount a file share from the command prompt
Use the Windows net use command to mount the Azure file share. Remember to replace the placeholder values in the following example with your own values. For more information about mounting file shares, see Use an Azure file share with Windows.
net use <desired-drive-letter>: \\<storage-account-name>.file.core.windows.net\<share-name> /user:Azure\<storage-account-name> <storage-account-key>
Configure NTFS permissions with icacls
Use the following Windows command to grant full permissions to all directories and files under the file share, including the root directory. Remember to replace the placeholder values in the example with your own values.
icacls <mounted-drive-letter>: /grant <user-email>:(f)
An other option with Azure files is Connect your Azure files to the DFS server
First I had to play a bit with the naming convention as the root of the file is not the share.
Below is the azure folder. so the share name would be \\storfileserver20.file.core.windows.net\blogshare03
As I use now the internal DNS and with the DFSN link
I can do domain name \ share and the files are being placed on the Azure file share. here you can also see that the naming is one step deeper. in the domain share name then there is the linked folder to the Azure Files.
On the time that I wrote this blog the Azure files snapshots came also GA.
there is no scheduled counter behind this. just press and shoot but with an script or automation account you can create nice solutions to keep your files save.
Hope this blog is helpful, It helped me to play with this and got some other ideas than just pasting the net use command to a device and then place the files. still there is nothing wrong with that.
Follow Me on Twitter @ClusterMVP
Follow My blog https://robertsmit.wordpress.com
Linkedin Profile Robert Smit MVP Linkedin profile
Google : Robert Smit MVP profile





























On prem AD is still in preview, only ADDS is GA.
Hi
I am trying this….and getting an error using the “New-AZDnsForwarder” command. Error is: Get-ArmTemplateObject : A parameter cannot be found that matches parameter name ‘Depth’.
I am using the template v.0.2.3
So the last forwarder isnt created……can you show me the result a bit more detailed, so that is possible to do this manually?
Best,
Lutz
the Powershell modules must have the latest version also the az.accounts need to be on the latest version. But often I noticed that with all ned versions nameing is also changing, ;-( first it was name then accountname now it is name again.
you can set this forwarder also in the dns by hand name is core.windows.net and IP 169. thats all.
must work I used this this week and it worked.
Hi Robert,
I am actually in the middle of setting this up but getting the traffic through the tunnel is actually a challenge at the moment. If I want to do this completely through the GUI is there a way for that aswell?
Thanks in advance.
Hi thanks for reading my blog, short answer no there is no GUI only the hybrid domain is powershell only. But if you are using azure domain services it can be domain only as there is a check box on do domain join on storage account but is a different approach https://docs.microsoft.com/en-us/azure/storage/files/storage-files-identity-auth-active-directory-domain-service-enable?tabs=azure-portal
Great Break Down
We have been using this exact workflow in production for clients for about 6 months. Cost of Azure VPN Bandwidth was much less than increasing on-premise spend to account for increased remote workers. If they return to Office, use DFS to change back to On Prem Azure File Sync Appliance, retaining Failover Ability to cloud. Biggest issue is that Azure Files only processes changes on the Native volume every 24 hrs. The AFS appliance pushes changes when dedicated on synced volume. Have you played around with any successful scripts or tasks to increase the frequency of the sync time between the AF and AFS appliances?
Hi, thanks for reading my blog. there are a couple of links and maybe you have already seen them.
Enable immediate sync after changes on the Azure file share for Azure File Sync
Invoke-AzStorageSyncChangeDetection
With the Invoke-AzStorageSyncChangeDetection you can trigger the change. but I did not come across a situation that this was needed. looking forward to hear your solution if it is other than the Invoke-AzStorageSyncChangeDetection.
Have you had any success in setting up AADDS on Azure Files with private endpoint to be authenticated? I can authenticate using the public name *****.file.core.windows.net but unable to authenticate when going through *****.privatelink.file.core.windows.net
yes this works perfectly. but have you add the fileshare to the AADS and give access rights on the share ? first join with key account and add NTFS permissions ? seems like that is your issue. there are no AADDS rights on the Share. or are you using a domain controller then you must user the hybrid powershell script.
Thanks Robert, will test this out and let you know. I had looked at this in the past. Was hoping the AFS File Locking solution would address this but it looks like that may be for AFS servers only and not the root Azure Files share, which obviously becomes a cost proposition to run a AFS server in Azure alongside the root share.
Make sure your DNS is set up with Azure DNS forwarding and that the Private endpoint is added as an A record to PrivateLink.yourdomain.com in your custom (windows) DNS config. Also remember that Azure files has both a Azure AD IAM and AD DS level of access. Ideally the IAM and AD DS levels match and all accounts are syncronized with Azure AD Connect. Most of our connection issues have been with issues around IAM/Azure AD and AD DS NTFS being disjointed in some way.
This article was very helpful. Thank you! This works perfectly in the office where the laptops are connected to an AD domain controller. But I would also like users to be able to use the Azure File Share at home without a VPN connection or something like that. That does not work. Users can only access/authenticate if connected to our on-premise domain. I’m fairly new to Azure AD and I’m stuck. Is there a workarround for this?
Hello Wouter this works also as you can see in the image https://i0.wp.com/scom.aca-computers.nl/image/Azure-Files_9BAC/image111_thumb.png?zoom=2 your dns need to have some extra settings and the Azure AD and the local AD need to be the same. synced with ad connect.
Hi Robert,
I am in the middle of trying to get rid of our on-prem file servers to use Azure File Shares.
I have Shares setup and computer Accounts in AD, I have copied files and ACLs using rocopy. I have 2 items left:
– do private endpoints require a VPN connection to Azure?
– Any ways I can automate share mounting? We currently use GPP based on AD security groups
I would use a small powershell script that mounts the drive letter on your system. and place that in a gpo